
PHP Intrusion Detection System: Website Security
PHP Intrusion Detection System Website Security The hacking threat grows in tandem with the size and complexity of the digital world. Web application security measures must be strong to prevent these attacks. Using a PHP Intrusion Detection System is one example of this precaution.
intrusion Detection: A Primer
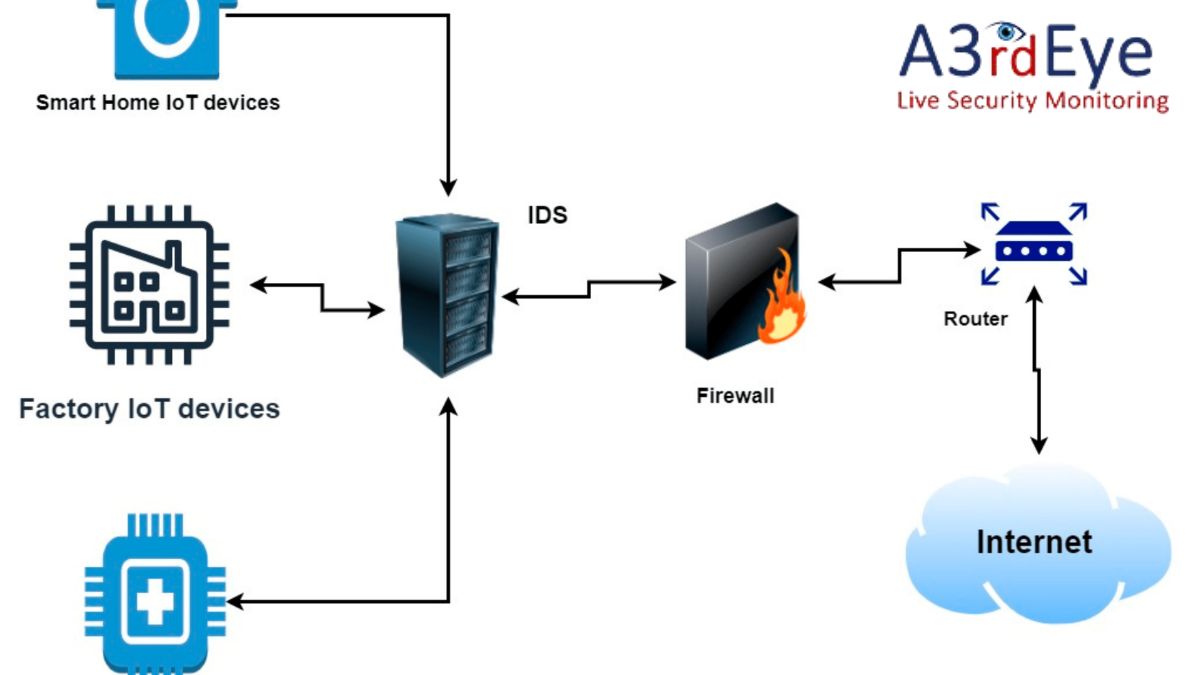
Intrusion Detection Systems (IDS) are programs that keep an eye out for breaches in security by keeping tabs on network traffic or host actions. Both network-based and host-based IDSs are common.
Intrusion Detection System Varieties
Network intrusion detection systems (NIDS) look at network traffic for anomalies that could indicate an active attack. In contrast, host-based intrusion detection systems (HIDS) examine behavior on specific hosts to identify malicious acts.
Contrasting network-based IDS vs. host-based IDS
While NIDS excels at spotting threats that span an entire network, HIDS shines when uncovering intrusions on a single machine.
An Overview of the PHP Intrusion Detection System
Just what is a PHP intrusion detection system?
Web applications written in PHP can benefit from PHP IDS because it is a security system tailored to detect malicious or unauthorized behavior. It’s like having a watchful guard at your door, checking and analyzing all incoming and exiting data at all times.
The Role of PHP IDS in Website Protection
To prevent SQL injection, cross-site scripting (XSS), and other web application security threats, PHP intrusion detection systems are essential. By locating and neutralizing these risks, sensitive data is protected against intrusion.
PHP Intrusion Detection System Operation
Signature-based and Anomaly-based detection are the two main detection methods used by PHP IDS.
Analysis of Molecular Signatures
Signature-based detection is like antivirus software, searching for previously identified threats. When it detects an attack signature in the incoming traffic, it sends out an alarm.
Identifying Unusual Patterns
In contrast, anomaly-based detection looks for unexpected changes in your app’s behavior. It provides a standard for conduct and triggers an alarm if any actions go against this standard.
The Installation and Configuration of PHP IDS
Integrating PHP IDS into your application’s coding is part of the setup process. Modifying your current code only a little is usually all that is needed. Once installed, the IDS can be tweaked to meet the needs of your app’s unique security setup.
Modifying Preset Guidelines for Your Program
You can modify PHP IDS’s detection rules to suit your specific software better. This prevents the algorithm from erroneously flagging legal behavior as suspicious.
PHP IDS’s Advantages
Online Threat Detection
PHP IDS is always active, watching your program in real-time. This guarantees that dangers are identified and mitigated as soon as possible.
Security against Both Common and Rare Dangers
Your application will be safe from known and unknown attacks using PHP IDS’s signature-based and anomaly-based detection.
IDS Best Practices in PHP
Upkeep and Updates on a Schedule
Maintaining a secure PHP IDS requires applying the most recent security updates and integrating the most recent threat intelligence feeds. The system’s ability to detect new threats depends on regular maintenance.
Shared Analysis of Dangerous Situations
By connecting to CTI networks, you may leverage the expertise of thousands of security experts to improve the performance of your PHP IDS.
Difficulties and Constraints
Negative and positive false results
PHP IDS may produce false positives (misclassifying safe traffic as malicious) or false negatives (missing real threats).
High Demand on Available Resources
Computing resources are needed for implementing an IDS, especially PHP IDS. It is crucial to check that your infrastructure can handle the extra traffic.
Predictions for the Future of Machine Learning Integration in PHP IDS
PHP IDS will soon be able to detect better complex and ever-changing threats thanks to the incorporation of machine learning methods.
Support for Behavioral Analysis
To uncover anomalies that conventional approaches overlook, future versions of PHP IDS will place more emphasis on sophisticated behavior analysis.
Conclusion
When it comes to protecting your website from the ever-changing threats in the world of web security, a PHP Intrusion Detection System is an absolute must-have—maintaining the security and privacy of your online apps through vigilant monitoring and prevention of malicious attempts.
Does PHP IDS work with every kind of website?
Because of its flexibility, PHP IDS may be configured, and rules can be modified to fit a wide range of use cases.
Can other preventative measures be abandoned in favor of PHP IDS?
PHP IDS is not a replacement for other security measures; instead, it should be used with other measures, such as secure code and frequent updates.
To what extent can PHP IDS block zero-day exploits?
PHP IDS’s core strength is in identifying known attack patterns, but it can also give some protection against zero-day attacks through anomaly detection.
What is the recommended schedule for updating the PHP IDS rules?
Consistent upkeep is required, ideally in tandem with new information about potential dangers. While monthly updates are typical, more frequent updates may be necessary in high-risk settings.
Is PHP IDS a “set it and forget it” thing?
Instead, PHP IDS must be constantly checked, maintained, and updated when new threats emerge.
PHP Intrusion Detection System Website Security

