
Security Integration: How to Safeguard Your Investments
Security Integration: How to Safeguard Your Investments has risen to the forefront of concerns for consumers, companies, and governments alike in today’s ever-changing technology environment. Organizations are realizing they need a holistic strategy to security that integrates diverse measures to successfully defend their assets in light of the proliferation and sophistication of threats. The concept of security integration is examined in this article, along with its significance, important components, benefits, problems, best practices, real-world examples, and future trends.
Introduction to Security Integration
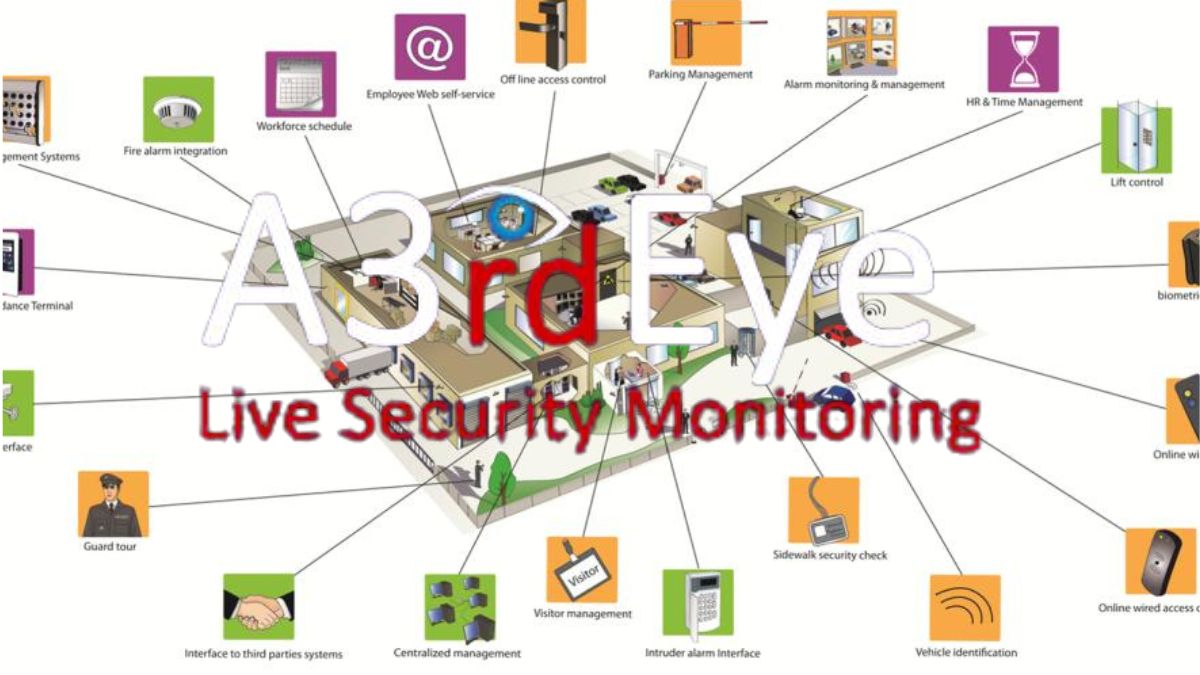
Security Integration: How to Safeguard Your Investments security measures are combined into one cohesive whole, this is known as security integration. The end goal is to establish a unified and interdependent security ecosystem that strengthens defenses, tightens up weak spots, and heightens awareness of the big picture. Detecting, responding to, and mitigating risks is made easier when physical security, cybersecurity, and data/network security are all integrated.
Importance of Security Integration
Physical Security Integration
Access control, video surveillance, intrusion detection, and perimeter security are all examples of physical security systems that can benefit from integration. Companies can prevent or quickly respond to security breaches by keeping tabs on who enters and leaves their buildings.
Cybersecurity Integration
When it comes to protecting digital assets from threats like hacking, data breaches, and virus attacks, cybersecurity integration is key. This entails doing things like installing firewalls, IDSs, antivirus software, secure authentication techniques, and training employees to be aware of potential threats.
Data and Network Integration
Integrating data and networks safeguards data during its journey across a network and its subsequent storage and retrieval. This requires the use of cryptography, safe data transfer protocols, network segmentation, DLP tools, and cloud storage solutions.
Benefits of Security Integration
Enhanced Threat Detection and Response
Organizations can improve their ability to quickly detect and respond to security problems by integrating security systems and processes. Integrated systems reduce the possibility of undiscovered security breaches by facilitating enhanced monitoring, event correlation, and automated threat response.
Improved Efficiency and Cost Savings
The integration of security measures reduces inefficiencies and saves money by doing away with unnecessary steps. Organizations may better allocate resources and respond to threats with the help of centralized management, automation, and intelligent analytics.
Streamlined Operations and Management
Integrating security systems streamlines administration and reduces the complexity of daily operations. Organizations can save time and effort by using a centralized platform that provides a bird’s-eye view of their whole security infrastructure. As a result, security teams are better able to work together and make use of available resources, and incident response times are reduced.
Challenges in Security Integration
There are many positive outcomes that can result from integrating security, but there are also obstacles that must be overcome.
Complexity and Compatibility Issues
When dealing with legacy systems or solutions from several manufacturers, it might be difficult to integrate various layers of protection. Planning, system design, and vendor cooperation are all essential for ensuring compatibility, easy data sharing, and interoperability.
Training and Skill Requirements
To manage and run integrated systems effectively, people must be well-trained in security integration. In order to maximize the benefits of integrated security solutions, businesses should engage in training programs to increase the security expertise of their staff.
Scalability and Future-proofing
There needs to be a scalable and future-proof approach to security integration as businesses expand and adopt new technology. Without sacrificing security, integration frameworks must adapt to shifting security needs, new types of threats, and emerging technologies.
Best Practices for Successful Security Integration
Organizations can improve the efficiency of their security integration by adhering to these guidelines.
Conducting Comprehensive Risk Assessments
Risk assessments should be performed to identify potential threats, weaknesses, and key assets before adopting security integration. This assessment is useful for setting priorities and allocating money for security initiatives.
Establishing Clear Objectives and Requirements
Defining clear objectives and requirements is crucial for successful security integration. Organizations must outline their security goals, determine specific integration needs, and establish measurable performance metrics to evaluate the effectiveness of the integrated solution.
Collaborating with Stakeholders and Experts
IT teams, security staff, vendors, and management are just some of the groups that need to work together to successfully integrate security. Experts and consultants in the field of security integration might be brought in to offer guidance and increase the likelihood of a smooth rollout.
Implementing Robust Security Policies and Procedures
Integrating security successfully requires comprehensive security policies and processes. If businesses want to implement security measures consistently, they need to create rules, access control methods, incident response protocols, and employee training programs.
Regular Testing and Evaluation
Maintaining the efficacy of security integration requires constant testing and evaluation. Organizations should perform penetration tests, vulnerability assessments, and system audits to proactively find and fix security flaws.
Real-world Examples of Effective Security Integration
Several businesses have improved their security by implementing security integration. To better monitor employee access in real time and respond swiftly to threats, XYZ Company, for instance, connected their physical access control system with their cybersecurity infrastructure. ABC Bank has a unified security information and event management (SIEM) system in place, which allows for faster threat detection and incident response by correlating data from many security systems.
Future Trends in Security Integration
Security Integration: How to Safeguard Your Investments New technologies and risks force constant change in the security integration industry. Future developments to keep an eye on include the widespread adoption of cloud-based security solutions, the use of blockchain technology to improve data integrity and secure transactions, and the incorporation of artificial intelligence and machine learning algorithms for intelligent threat detection and automated response.
Conclusion
Security Integration: How to Safeguard Your Investments today’s increasingly interconnected world would do well to adopt a security integration strategy. Organizations can attain a holistic and preventative security stance by combining physical security with cybersecurity and data/network security. Although obstacles may exist, implementation success can be ensured by adopting best practices and working with stakeholders and experts. Maintaining strong security measures and protecting vital assets will require keeping up with evolving trends in security integration as technology and threats develop.
How does security integration vary from more conventional methods of security?
Frequently, physical and digital security are treated as separate entities in conventional security models. Instead, a comprehensive and preventative security approach can be achieved through security integration, which brings together many security systems, technologies, and practices under a single umbrella.
Can the new security measures be integrated with the older ones?
Legacy systems are compatible with security integration. However, it’s possible to run into compatibility and interoperability problems, which means you’ll need to undertake some planning, system design, and vendor coordination to make sure everything goes smoothly.
How does integrating security boost productivity?
Centralized management, streamlined procedures, and the removal of redundant steps all contribute to increased productivity thanks to security integration. It helps businesses streamline operations by automating routine procedures and detecting and fixing security flaws in record time.
Is future-proof security integration a possibility?
Security Integration: How to Safeguard Your Investments it must be scalable and adaptable in order to be a successful security integration. Without sacrificing security, integration frameworks must adapt to shifting security needs, new types of threats, and emerging technologies.
When it comes to security, what are the emerging trends?
Artificial intelligence (AI) and machine learning (ML), growing usage of cloud-based security solutions, and blockchain technology to improve data integrity and secure transactions are all trends that will likely become more common in the near future.
Security Integration How to Safeguard Your Investments

